
Terraform CI/CD: A Practical Guide to Infrastructure Automation
Understanding Infrastructure as Code Pipelines
Infrastructure as Code (IaC) pipelines differ fundamentally from application CI/CD. With Terraform, you're managing real infrastructure resources that have immediate cost and security implications. A misconfigured security group or an incorrect resource sizing can have significant consequences.
What Makes Terraform CI/CD Different?
Infrastructure as Code (IaC) pipelines are fundamentally different from traditional application CI/CD pipelines. When deploying applications, you're typically working with containerised services or isolated deployments. However, with Terraform, you're managing actual infrastructure resources that have real costs, dependencies, and production impact.
This distinction means that a mistake in your Terraform pipeline could potentially affect your entire infrastructure - from networking to security groups to production databases. It's like the difference between updating the furniture in a house (application deployment) versus modifying the house's foundation and support structures (infrastructure changes).
This critical difference requires a specialised pipeline with additional safety measures, validation steps, and careful controls. Our workflow diagram illustrates how these elements work together to ensure safe and reliable infrastructure management.
State Management: The Foundation
The bottom section of our diagram shows what might be the most crucial component of Terraform operations: state management infrastructure. This foundation ensures that all changes are tracked and coordinated properly.
Remote State Storage
Think of remote state storage as the single source of truth for your infrastructure. It's like having a master blueprint of your entire infrastructure that everyone refers to and updates. This system:
- Maintains detailed records of all infrastructure resources in a centralized S3 bucket
- Enables team collaboration by providing a shared reference point for all infrastructure states
- Keeps a history of infrastructure changes, making it possible to track how resources evolved
- Provides backup and recovery capabilities in case of accidents or failures
- Ensures that everyone is working with the same infrastructure information
Modern infrastructure teams typically use S3 for state storage:
terraform {
backend "s3" {
bucket = "company-terraform-state"
key = "environments/${var.environment}/terraform.tfstate"
region = "us-west-2"
dynamodb_table = "terraform-locks"
encrypt = true
}
}
State Locking
State locking is the traffic control system for infrastructure changes. Without it, multiple teams could unknowingly try to modify the same resources simultaneously. The locking mechanism:
- Uses DynamoDB tables to implement a robust locking system
- Prevents concurrent modifications that could lead to conflicts or inconsistencies
- Queues changes so they proceed in an orderly fashion
- Maintains state consistency by ensuring only one change process runs at a time
- Provides clear visibility into who is making changes and when
DynamoDB provides locking to prevent concurrent modifications:
resource "aws_dynamodb_table" "terraform_locks" {
name = "terraform-locks"
billing_mode = "PAY_PER_REQUEST"
hash_key = "LockID"
attribute {
name = "LockID"
type = "S"
}
}
The Three Pillars of Infrastructure Pipeline
Looking at our workflow diagram, we can identify three main components that work together to ensure safe infrastructure deployments. Each pillar serves a specific purpose and contains crucial safeguards.
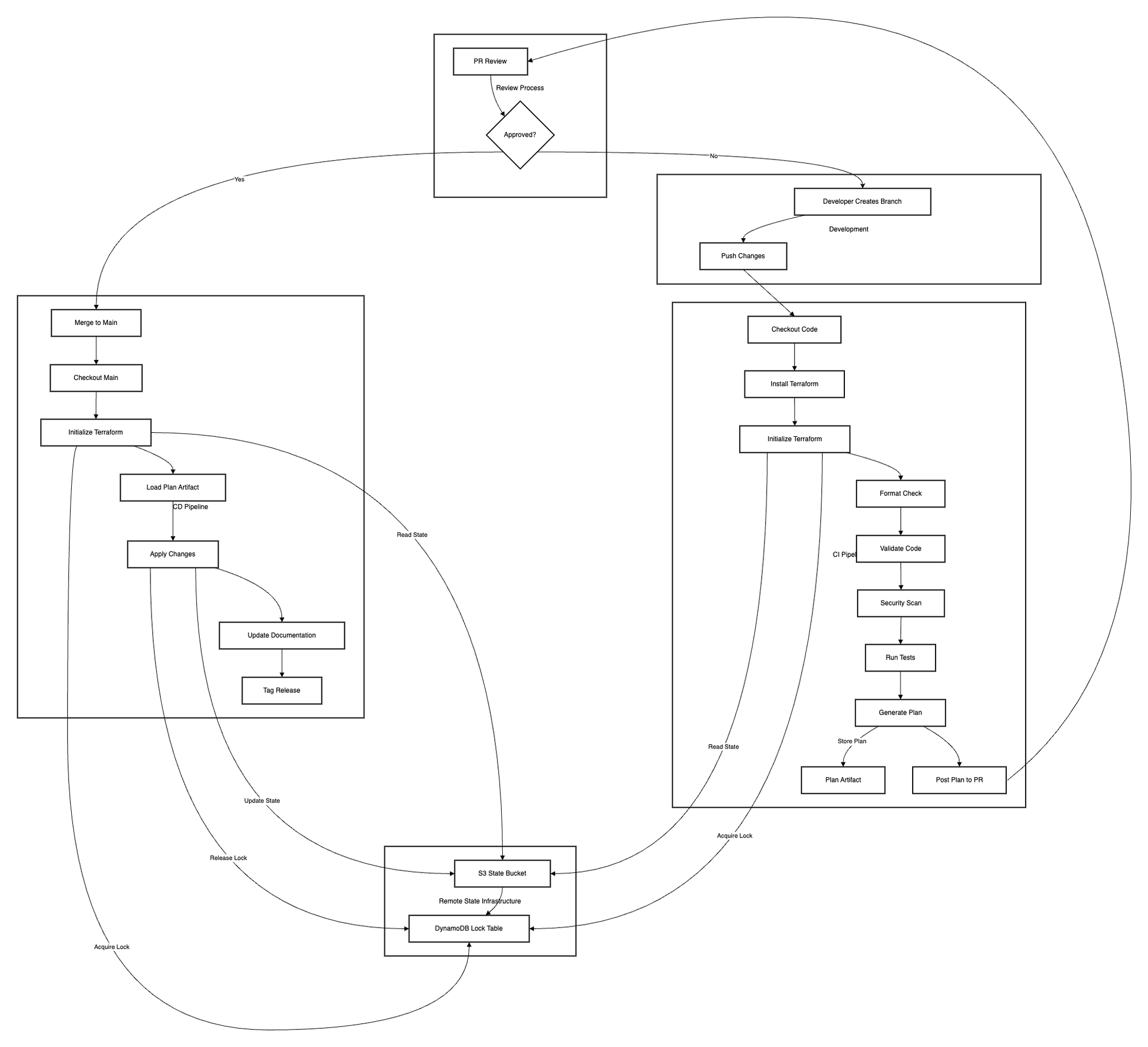
1. Development Flow
The right side of our diagram showcases the developer's journey through infrastructure changes. This section emphasizes the importance of proper preparation and validation before any changes reach production.
When developers need to make infrastructure changes, they:
- Create new branches specific to their infrastructure changes, keeping modifications isolated and trackable
- Push their changes to trigger a series of automated checks that validate basic correctness
- Run through multiple security scans that check for common misconfigurations and vulnerabilities
- Generate infrastructure plans that show exactly what will change in the environment
This process is similar to traditional software development but includes infrastructure-specific checks. For example, cost estimation helps prevent accidental resource provisioning that could lead to unexpected bills, while security scans ensure no sensitive data is exposed through infrastructure configurations.
2. Review Gateway
The central section of our diagram represents perhaps the most critical control point in the entire process. This gateway ensures that all changes receive proper scrutiny before implementation.
During the review phase:
- Team members examine proposed infrastructure changes with an understanding of their broader impact
- Costs are evaluated not just for the immediate change but for long-term implications
- Security considerations are assessed, including potential attack vectors or compliance violations
- Compliance requirements are verified against company and regulatory standards
- Decisions to approve or reject changes are made based on comprehensive evaluation
This step is crucial because infrastructure changes often have wider-reaching implications than application code changes. A simple change to a security group rule, for instance, could potentially expose sensitive services to the internet.
3. Deployment Process
The left section of our diagram illustrates how approved changes safely make their way into production. This process ensures that what gets deployed matches exactly what was reviewed and approved.
The deployment process:
- Merges approved changes into the main branch, maintaining a clean history of infrastructure evolution
- Loads the exact plan that was reviewed, preventing any last-minute modifications
- Applies changes in a controlled manner with proper error handling
- Updates documentation to reflect the new state of infrastructure
- Creates release tags for future reference and rollback capabilities
This systematic approach ensures that infrastructure changes are traceable, reversible, and properly documented.
Why This Workflow Matters
This carefully designed pipeline addresses several critical challenges in infrastructure management:
Safety
Infrastructure changes can have far-reaching consequences, making safety paramount:
- Multiple validation stages catch potential issues early
- Required peer reviews ensure changes are thoroughly vetted
- Automated security checks identify vulnerabilities before they reach production
- Plan verification ensures that what gets deployed matches what was reviewed
- Change tracking helps identify the source of any issues that arise
Consistency
A standardized process ensures reliable and predictable infrastructure management:
- All changes follow the same validation and approval steps
- Automated checks maintain quality standards
- Version control provides a clear history of changes
- Documented approvals ensure accountability
- Standard workflows reduce human error
Auditability
In regulated environments, being able to track and explain changes is crucial:
- Every change is tracked in version control
- Releases are tagged for easy reference
- State versions provide a history of infrastructure evolution
- Access logs show who made what changes and when
- Approval records demonstrate proper oversight
Common Challenges and Solutions
State Management
Managing state effectively requires careful planning:
- Implement remote state from the beginning to avoid migration headaches
- Use proper locking to prevent concurrent modifications
- Maintain regular state backups for disaster recovery
- Separate workspaces clearly to avoid environmental confusion
- Monitor state access to detect unauthorized changes
Process Control
Maintaining control over infrastructure changes requires robust processes:
- Enforce branch protection to prevent unauthorized changes
- Require peer reviews to ensure proper oversight
- Automate security scans to catch vulnerabilities early
- Monitor state access to detect potential issues
- Implement emergency procedures for critical fixes
Team Collaboration
Effective team coordination is essential for successful infrastructure management:
- Establish clear ownership rules for different infrastructure components
- Document review processes to ensure consistent evaluation
- Maintain detailed change history for troubleshooting
- Conduct regular team training on infrastructure best practices
- Create clear escalation paths for critical issues
Conclusion
A well-designed Terraform CI/CD pipeline is more than just automation - it's a comprehensive system that ensures infrastructure changes are safe, controlled, and auditable. Understanding this workflow helps teams implement infrastructure changes with confidence while maintaining security and compliance requirements.
The careful balance between automation and control provides the guardrails needed for safe infrastructure changes while maintaining efficiency and auditability. When implemented properly, this workflow becomes an essential tool for modern infrastructure management, enabling teams to evolve their infrastructure confidently and securely.
Comments ()